Member-only story
Many organizations get access to their AWS resources using Direct Connect or a site to site VPN. This is great if you have an on-premise network where you want your employees to have access to AWS services and resources without needing to go out to the Internet.
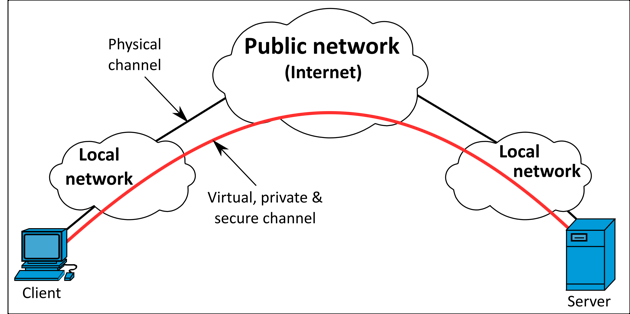
Image from Wikipedia
What if all your employees are remote and you effectively have no corporate network?
In this situation, a Direct Connect makes no sense as there is no corporate network. The same is true for a site to site VPN. Your DevOps teams may have access to the console, or to services through the AWS Command Line Interface (CLI) and software development kit (SDK).
The applications your employees use and the services you provide your customers may all be Internet-facing. However, the situation will arise when you need access to an EC2 or some other resource where you need a command line to resolve some issues. This is where the AWS Client VPN comes to the rescue.
Prerequisites
Before you jump into the console and try creating your Client VPN, there are some things you need to know and have available first:
- A server-side certificate;
- A client-side certificate if you are going to use mutual authentication;
- Information about your Active Directory server if you want to use username/password authentication;
- A Virtual Private Cloud (VPC) with at least one subnet;
- A CPN client application; and,
- Details about the networking configuration in your VPC.
We will walk through all the prerequisites as we embark on configuring the Client VPN. I should point out I will be discussing the use of mutual authentication in this article, and not Active Directory authentication.
How it works
AWS Client VPN allows a VPN connection from a device running VPN client software to the Client VPN endpoint created in your VPC. AWS Client VPN uses OpenVPN, so the native VPN services on systems like Microsoft Windows, and Apple macOS will not get you connected.
